Okta just squashed a particularly unusual bug in its software.
The xxx tv showdigital security management company posted a bug fix report to its website (as spotted by The Verge) letting users know that a glitch in the system that theoretically allowed bad actors to gain access to accounts had been ironed out. Sounds normal enough, right? Well, here's the kicker: The bug could've allowed someone to log into an account without entering the passwordas long as the username was 52 characters or longer.
"During specific conditions, this could allow users to authenticate by only providing the username with the stored cache key of a previous successful authentication," Okta wrote.
It should be re-emphasized that this is no longer a concern for Okta users. The bug has been fixed. Unfortunately, it existed in the system for about three months, as Okta's report said the software had been affected since July until someone noticed on Oct. 30. That's a very long time for such a vulnerability to be present, but it's unclear at this point if anyone was negatively affected by it.
Topics Cybersecurity
(Editor: {typename type="name"/})
 Wordle today: The answer and hints for March 5
Wordle today: The answer and hints for March 5
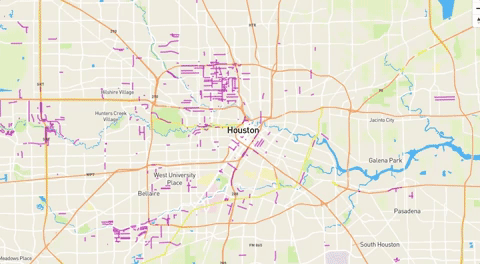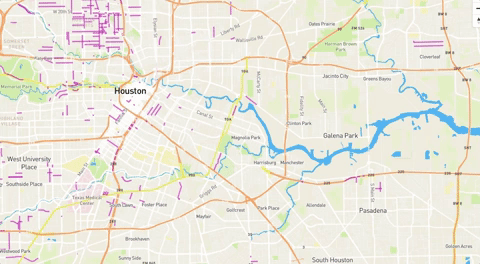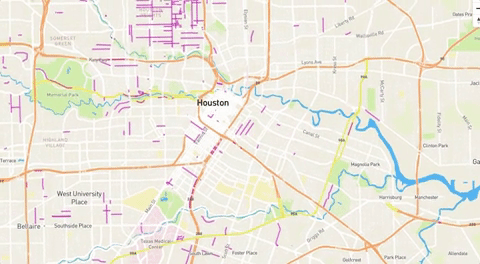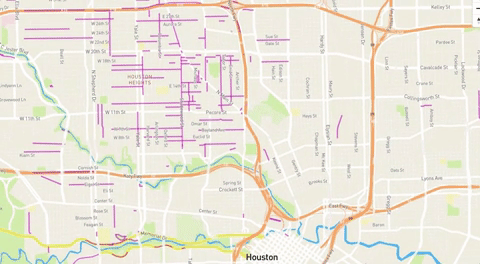 Crowdsourced project tracks Harvey
Crowdsourced project tracks Harvey
 Elon Musk sues OpenAI, wants it to go nonprofit again
Elon Musk sues OpenAI, wants it to go nonprofit again
 Best IPL deal: Save $80 on Braun IPL Silk·Expert
Best IPL deal: Save $80 on Braun IPL Silk·Expert
Sony launches new flagship XM6 headphones: Order them now
 Table of ContentsTable of ContentsOn May 15, Sony released its newest flagship headphones, the noise
...[Details]
Table of ContentsTable of ContentsOn May 15, Sony released its newest flagship headphones, the noise
...[Details]
Former Twitter/X executives sue Elon Musk for $128 million in unpaid severance
 Four former Twitter/X executives are suing both the company and its owner Elon Musk for over $128 mi
...[Details]
Four former Twitter/X executives are suing both the company and its owner Elon Musk for over $128 mi
...[Details]
Buy $60, get $15 off Unilever essentials at Amazon
 GET $15 OFF:As of March 5, you can score $15 off everyday essentials when you spend $60 on select Un
...[Details]
GET $15 OFF:As of March 5, you can score $15 off everyday essentials when you spend $60 on select Un
...[Details]
The people love 'Dune: Part Two'
 Anticipation for Dune: Part Tworan high here at Mashable, where my fellow staff members spent signif
...[Details]
Anticipation for Dune: Part Tworan high here at Mashable, where my fellow staff members spent signif
...[Details]
Seven Steam games whose reviews have changed a lot
Best Lego deal: Score the Lego Classic Large Creative Brick Box for 45% off at Amazon
 Legos know no bounds when it comes to creativity, imagination, or age. The price of a Lego set, howe
...[Details]
Legos know no bounds when it comes to creativity, imagination, or age. The price of a Lego set, howe
...[Details]
How to watch the total solar eclipse from anywhere on Earth
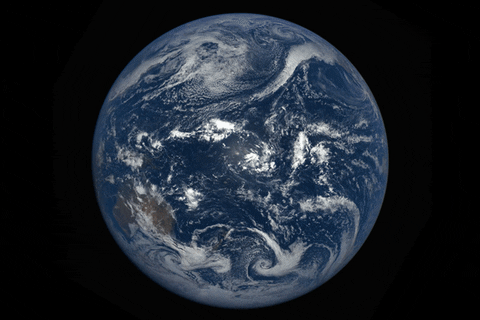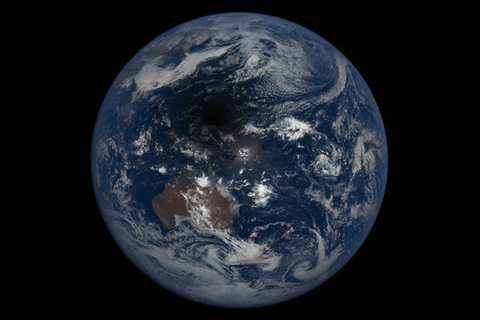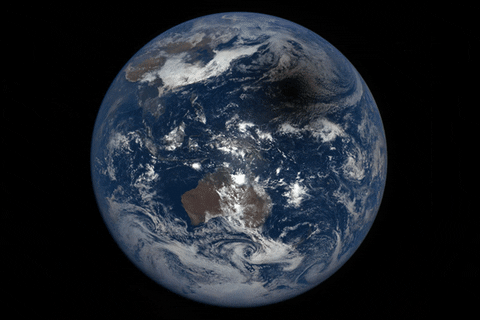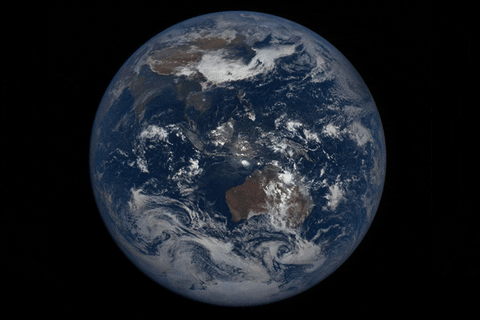 As the moon passes between the Earth and the sun, blotting out our nearest star on August 21, millio
...[Details]
As the moon passes between the Earth and the sun, blotting out our nearest star on August 21, millio
...[Details]
Here's all the cool stuff you can do on social media to celebrate the eclipse
 The total solar eclipse will be streamed, grammed, snapped, and shared. Monday's event is one of the
...[Details]
The total solar eclipse will be streamed, grammed, snapped, and shared. Monday's event is one of the
...[Details]
Musetti vs. Diallo 2025 livestream: Watch Madrid Open for free
 TL;DR:Live stream Musetti vs. Diallo in the 2025 Madrid Open for free on RTVE. Access this free stre
...[Details]
TL;DR:Live stream Musetti vs. Diallo in the 2025 Madrid Open for free on RTVE. Access this free stre
...[Details]
M3 MacBook Air: 3 new features you won't find on the M2 MacBook Air
 The new M3 MacBook Air, coming in two flavors —13-inch and 15-inch models — is hitting s
...[Details]
The new M3 MacBook Air, coming in two flavors —13-inch and 15-inch models — is hitting s
...[Details]
Your 'wrong person' texts may be linked to Myanmar warlord

Elon Musk's X has already backed off its new anti

接受PR>=1、BR>=1,流量相当,内容相关类链接。